
Behavioral-based detection and mitigation to defend against unknown zero-day attacks without impacting legitimate user experience

Automated signature creation and advanced challenge escalations to achieve the highest mitigation accuracy that can automatically mitigate unknown attacks and minimize the impact on legitimate traffic

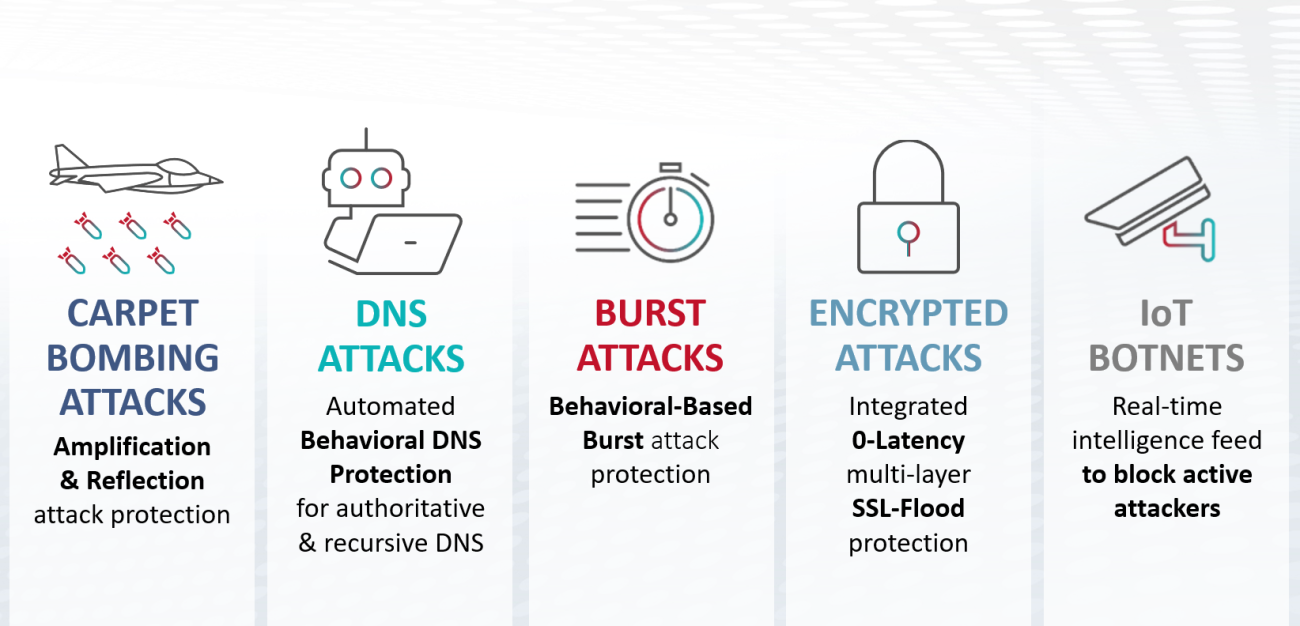
Detection and mitigation of today’s most advanced attacks, including Burst attacks, Domain Name System (DNS) amplification attacks, IoT botnet floods, Layer 3–7 and other crippling DDoS attacks



Detection and mitigation of today’s most advanced attacks, including Burst attacks, Domain Name System (DNS) amplification attacks, IoT botnet floods, Layer 3–7 and other crippling DDoS attacks
Patented behavior-based detection technology enables organizations to accurately detect attacks in real time while minimizing false positives.
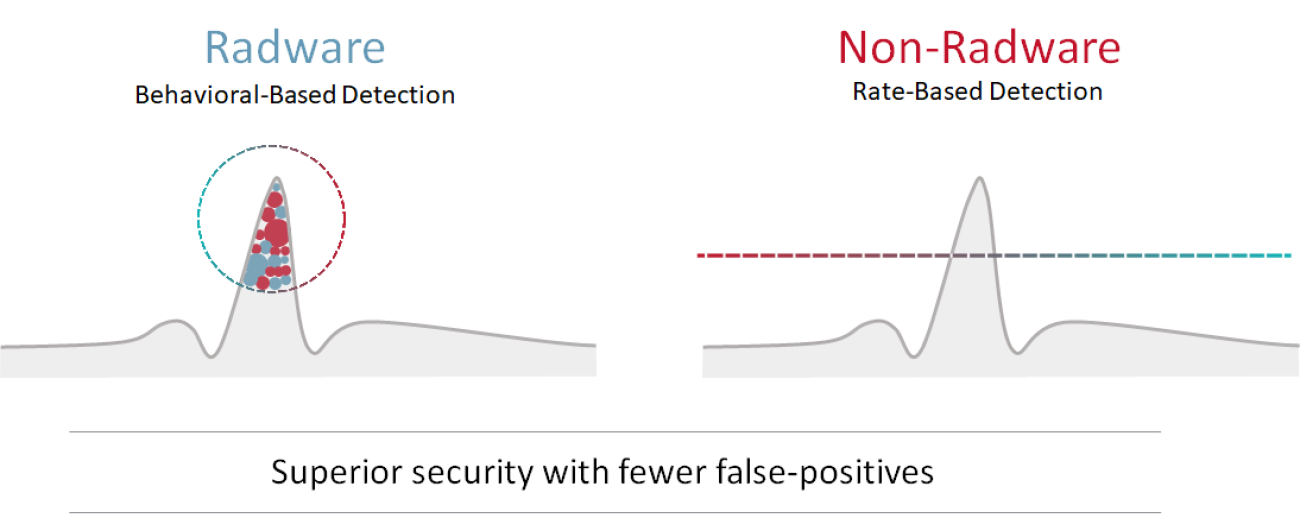





Patented behavior-based detection technology enables organizations to accurately detect attacks in real time while minimizing false positives.
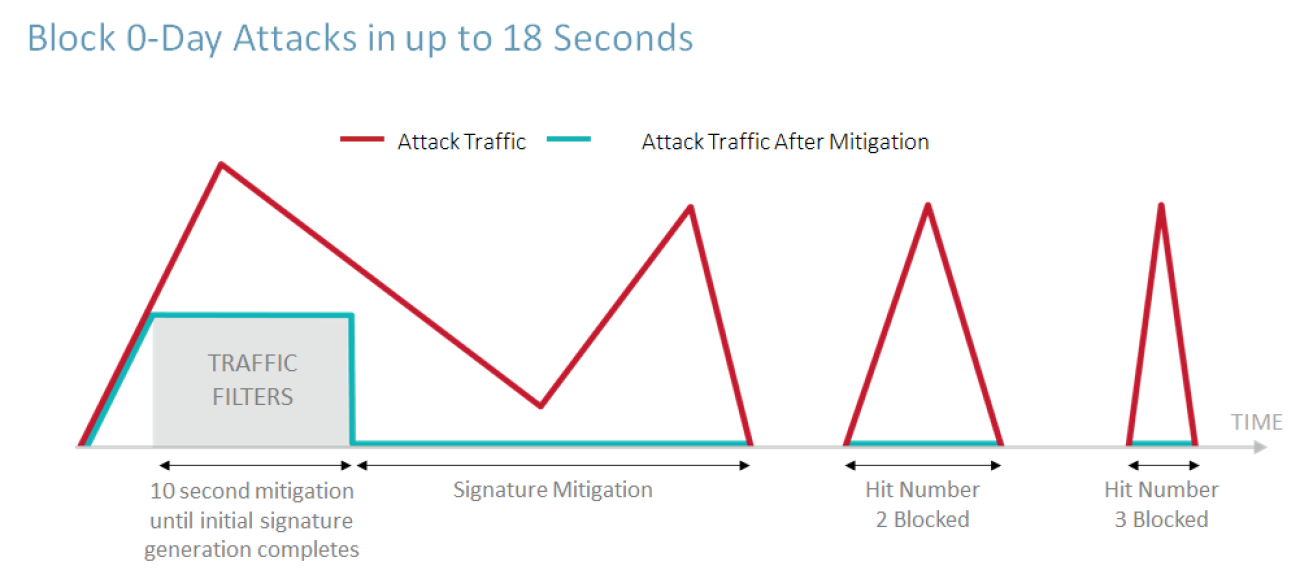


Attack signatures can be automatically generated to accurately protect from zero-day and unknown attacks. Within 18 seconds, DefensePro can detect, characterize and generate an optimal signature to block unknown attacks.



Attack signatures can be automatically generated to accurately protect from zero-day and unknown attacks. Within 18 seconds, DefensePro can detect, characterize and generate an optimal signature to block unknown attacks.
High-capacity keyless protection from SSL/TLS-based DDoS attacks without adding latency to customer communications and while preserving user privacy
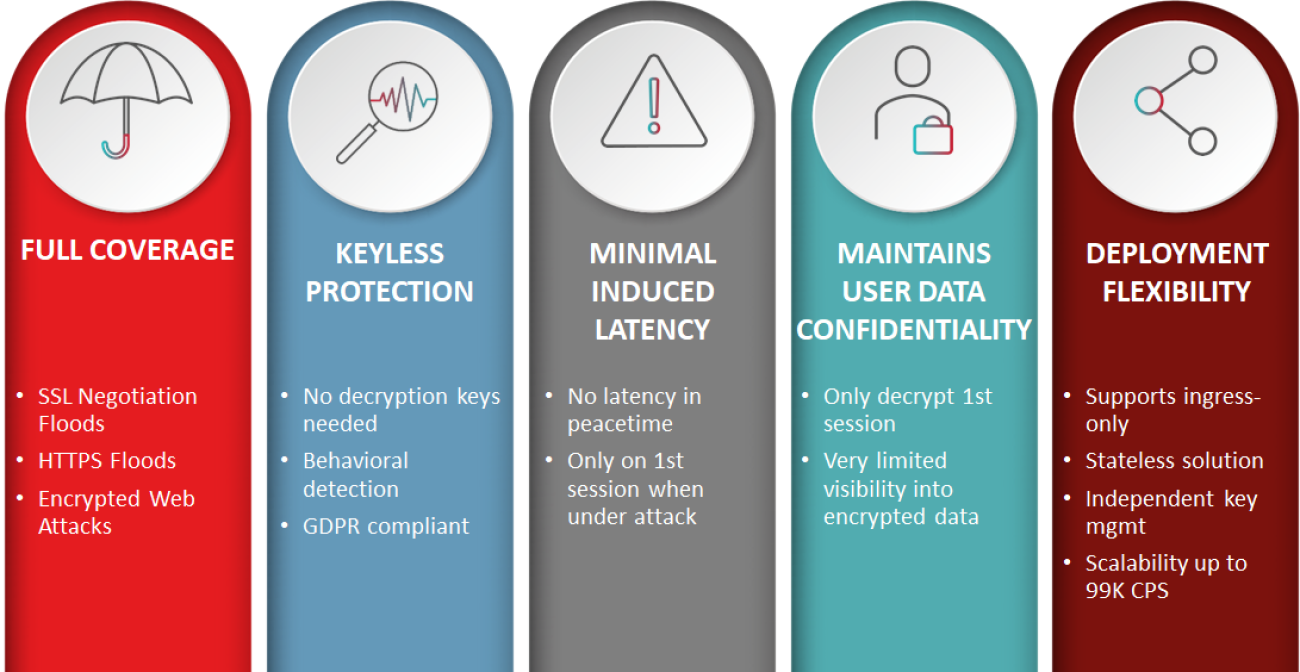





High-capacity keyless protection from SSL/TLS-based DDoS attacks without adding latency to customer communications and while preserving user privacy
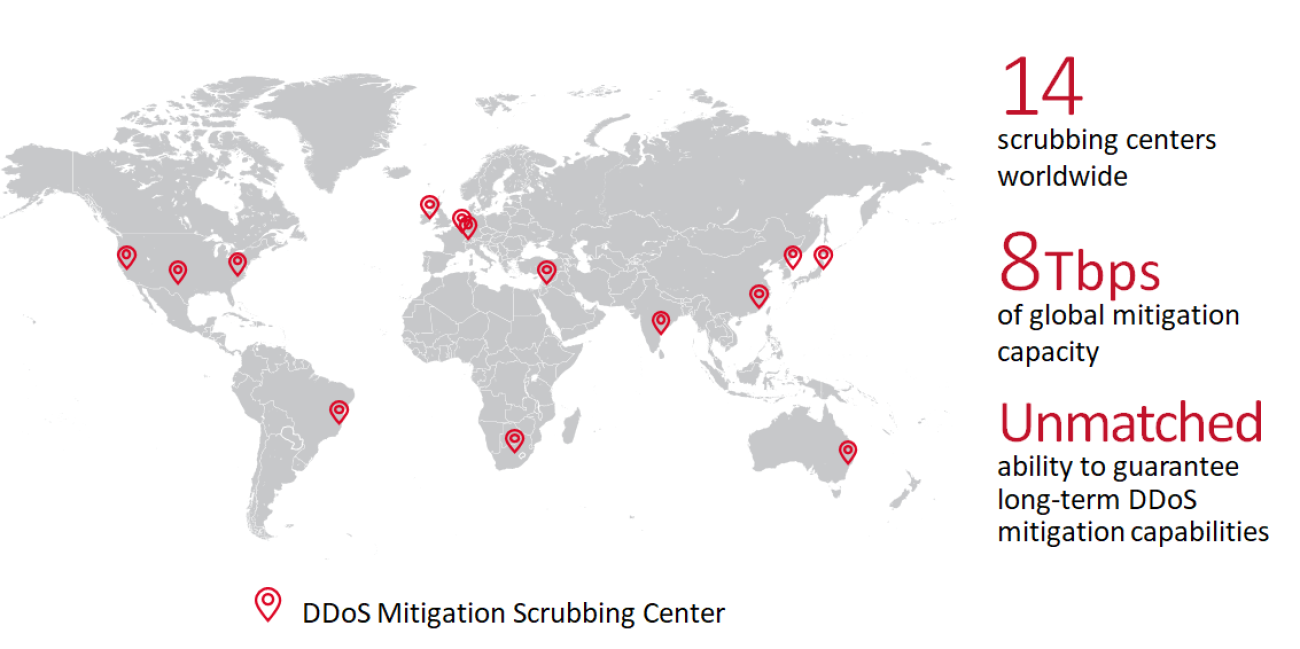


Multiple deployment options are available, with cloud-based, hardware-based and hybrid solutions to match any customer architecture or use case.



Multiple deployment options are available, with cloud-based, hardware-based and hybrid solutions to match any customer architecture or use case.
Sign up to receive the latest information from VNCS


© 2022 Vietnam Cyberspace Security Technology. All Rights Reserved