SERVICE
COMPROMISE ASSESSMENT
Experienced staff with high qualifications
VNCS owns a team of experts with many years of experience in the field of Information Security, well-trained in the field of information security, accompanied by security certificates from reputable organizations.

Proprietary technology
System Penetration Assessment Service – Compromise Assessment uses proprietary tools that automate investigation tasks and enable rapid assessment of network traffic and server-based artifacts — even on networks containing hundreds of thousands of systems.

Service operation according to professional deployment process
Standardized process from identifying weaknesses or existing security holes on the infrastructure, from which to evaluate the level and priority of existing security holes based on the level of vulnerability. impact, the importance of resources/assets in order to put solutions to overcome and minimize risks




Evidence of attack groups
We work with Mandiant team, use experience gained over hundreds of investigations when assessing networks for the presence of various indicators of compromise including:
– Re-used custom malware: Custom malware is often developed at great expense to the attack group. Consequently, they prefer to reuse it — or variants that have similar characteristics. Attack groups can oftentimes be discovered by identifying malware analyzed during prior investigations



Maintenance mechanism:
Several techniques can be used to establish and maintain an attacker’s existence in a system. Windows registry entries can store malicious code execution parameters, malicious code can be placed in the Startup folder, and legitimate system binaries can be trojanized. Recognizing what attack groups typically do allows us to look for signs of those mechanisms.









Peer-to-peer migration:
Most APT attack groups capture valid privileged credentials and use them to evaluate the environment. Knowing how they obtained those credentials and the tools they use to access other systems allows our experts to scour logs and forensic evidence of that attacker’s activity. .
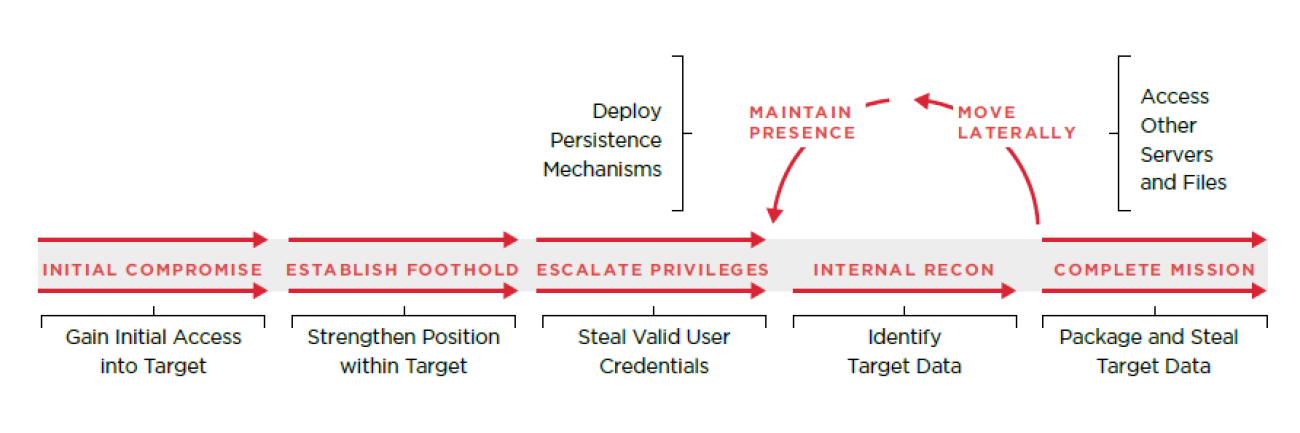


Designed to identify targeted attacks
Over the past few years, APT attack groups — often backed by criminal organizations or even countries — have targeted government agencies as well as private businesses and organizations. These attackers have managed to go undetected and can steal data for a long time. They develop custom malware themselves and use tactics that are difficult to detect with conventional methods.




